Retired Projects

CrashSimulator is a tool that replicates “real-world” testing for new and upgraded software without the complications of “real-world” deployment. The program enables software developers to identify vulnerabilities in product designs long before they are packaged and released.
Within every confusing piece of software code are small patterns that can lead developers to outputs that radically differ from what was intended. In studying these “atoms of confusion” we look to build a firm empirical foundation for reducing code confusion in software development and, thus, also reduce the frequency of buggy and malfunctioning programs.

Delivery of large chunks of content, such as video, accounts for a substantial percentage of all Internet traffic. This content is usually served by provider networks that contract with Internet Service Providers. CacheCash provides a similar service in which interested users run caches, and are incentivized to participate by receiving a crypto-currency (Cachecoin) in exchange for serving content to other users. Both cryptographic and economic techniques demonstrate that CacheCash users are either forced or economically incentivized to honestly serve content. Our analysis shows that CacheCash scales to meet the workload of even the most popular services used today. By building CacheCash, we intend to change CDNs by more readily and pervasively including end-user served content.
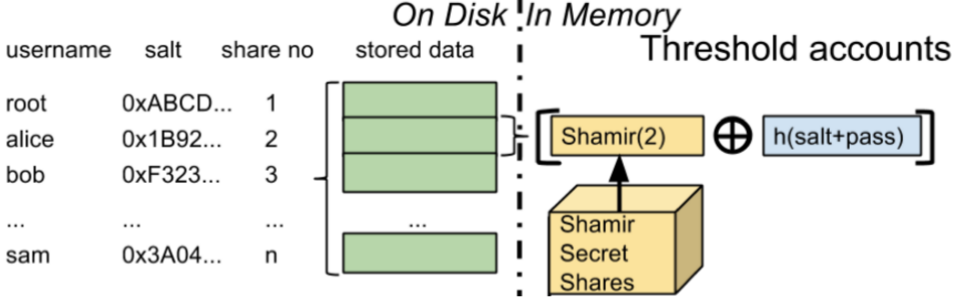
A password database disclosure can be devastating, costing companies billions of dollars in damages. PolyPasswordHasher offers a new approach to prevent attackers from finding out which passwords are being used. By interrelating stored password data, potential hackers are forced to crack passwords in sets. This increases the attackers’ level of difficulty, making a PolyPasswordHasher-enabled database very hard to breach, even for an adversary with millions of computers.
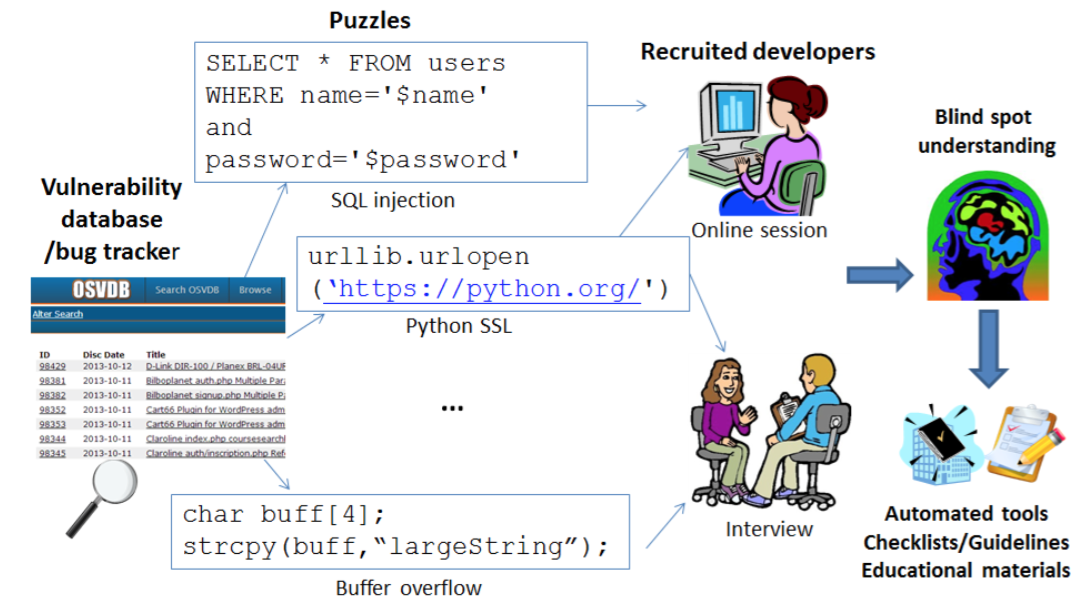
This project seeks to identify situations where security issues are created by the misunderstanding of APIs by developers. In particular, we are looking for security-related blind spots in popular Java and Python APIs as a way to more holistically find and address bugs.

Cloud computing can provide tremendous benefits due to its ability to offload computation on demand. However, cloud resources are often located far from users. The Seattle project enables users to securely share (and acquire) computing resources from their desktop, laptop, or smartphone in the same manner as with cloud computing. Seattle is used by educators, and for software development and research by thousands of people around the world.
Given the close proximity of smartphones to users, researchers would benefit from accessing smartphone sensors. By giving the user control over what amount and type of data is gathered from these sensors, Sensibility ensures the privacy of user information. Sensibility also has additional security protections that ensure the safety of the device, while giving researchers access to unique information.
NetCheck is a tool that can determine the cause of a failure in a networked application, without any application or network-specific knowledge, and without any modification to the application or its infrastructure. By treating an application as a blackbox, a diagnosis can be made using just a set of system call (syscall) invocation traces from the relevant end-hosts. By simulating the syscalls against a network model, syscalls that deviate from expected network semantics can be identified. In return, these deviations can be mapped to a diagnosis by using a set of heuristics.
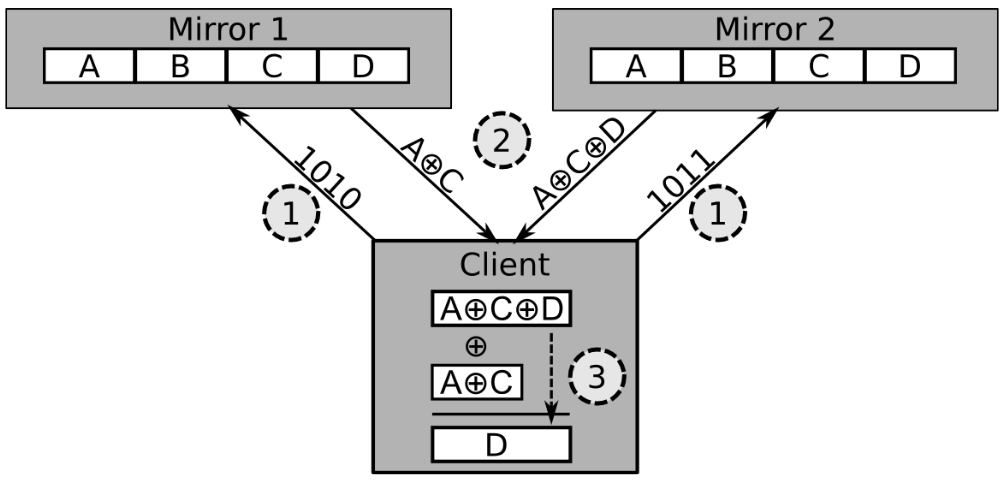
upPIR is a secure protocol that allows users to mask their information requests by privately retrieving information from a set of mirrors. By packaging the required information with other data that potentially could be requested, the user's preferences—and any assumptions that could be deduced from those preferences—remain hidden.

Virtual Secure Network (VSN) is a network service that provides remote users the security benefits of a managed (corporate/cloud) network, without sacrificing the faster Internet performance more typical of an insecure direct connection. A VSN is analogous to a Virtual Private Network (VPN) in that it offers security protections, such as firewalls, multiple Antivirus scanners, IDSs, and IPSs. However, VSN can guarantee lower costs for management, and better performance for its end users.